Back to Blog
NIST Digital Identity Guidelines: A Brief Summary
It’s been over half a decade since the National Institute of Standards and Technology (NIST) introduced groundbreaking changes to its password guidelines, yet a significant number of organizations are still clinging to antiquated security practices, often risking cybersecurity breaches. Here, we explore the gap between NIST’s cutting-edge guidelines and the reality of their implementation across organizations, highlighting an urgent call for modernization and enhanced risk management.
Embracing a New Shift
Released in June 2017, the final version of these guidelines, part of the esteemed NIST SP 800-63 series on Digital Identity Guidelines, represented a pivotal shift in our approach to password security, urging a reevaluation of lifecycle management strategies. The password guidelines we’ll discuss here are still in effect today and are crucial for maintaining robust cybersecurity protocols in the face of evolving threats from hackers and online attacks.
Gone are the days of insisting on complex passwords peppered with a mix of symbols, numbers, and letters (uppercase and lowercase), and the frequent resetting of passwords – practices once deemed essential for digital security. These guidelines ushered in an era that prioritizes user-friendly password policies, aligning with the latest insights into how better password practices enhance security and user experience, ultimately reducing the vulnerability to phishing attempts and brute force attacks.
Here, we’ll provide an insightful overview of the revised NIST password guidelines, examining the significant changes made since 2017 and their implications for federal agencies and organizations across various sectors. We’ll explore how these changes were driven by NIST’s findings on the human factors that often lead to the creation of weaker passwords, and discuss the new recommendations and the logic that underpins them as detailed in the NIST Special Publication 800-63B, titled ‘Digital Identity Guidelines’, along with its Appendix and FAQs. The following are the changes organizations should be aware of:
- Users no longer have to use special characters
Arbitrary password complexities that require users to combine special characters with alpha numerals have shown users may create worse passwords with lesser security, leaving them vulnerable to identity-proofing breaches.
As NIST explained in Appendix A: “Analyses of breached password databases reveal that the benefit of such rules is not nearly as significant as initially thought, although the impact on usability and memorability is severe.”
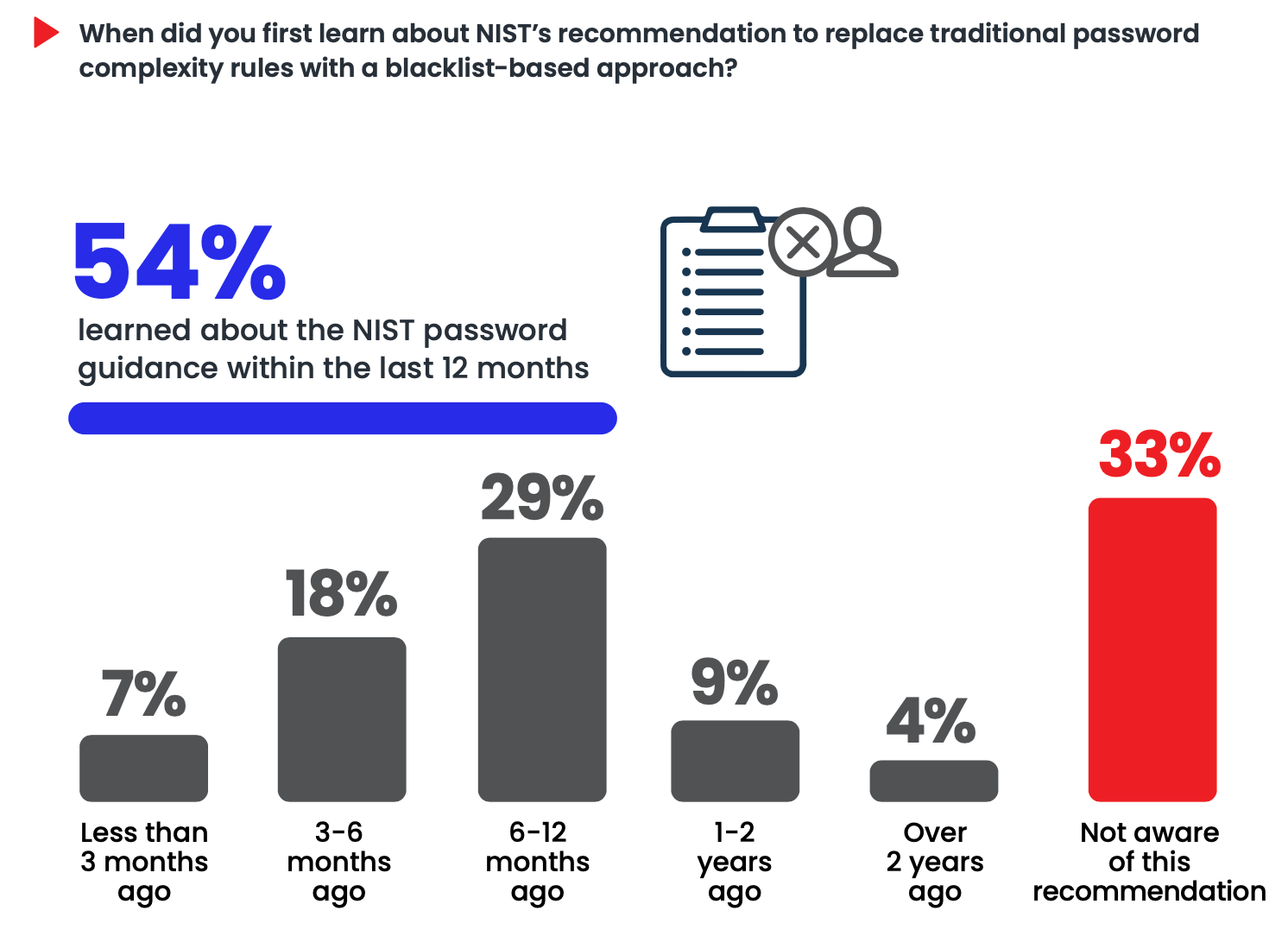
Enzoic’s 2023 Authentication Survey reveals that a significant 33% of organizations are not aware of NIST’s recommendation to abandon arbitrary password complexity rules.
- Users should be able to use all characters
NIST password guidelines now recommend that users create passwords using whatever combination of characters they can easily remember, facilitating the adoption of multi-factor authentication (MFA) and biometric measures for enhanced identity verification and authentication.
As NIST explains, “Many services reject passwords with spaces and various special characters. In some cases, the special characters that are not accepted might be an effort to avoid attacks like SQL injection that depend on those characters. However, a properly hashed password would not be sent intact to a database in any case, so such precautions are unnecessary.
Under the current guidelines provided in NIST SP 800-63B 5.1.1.2, NIST observes that users should be able to maintain passwords using regular characters provided, including spaces, although they highlight that repeated spaces should ideally be trimmed to mitigate risks associated with offline attacks.
- It is reasonable to copy and paste passwords
Under the previous guideline versions, NIST was against enabling paste features when typing passwords. This is no longer the case. The revised guidelines recommend allowing paste. Being able to paste into a password field facilitates the use of password managers, a well-advised practice. Password manager utilizes a single master password to access stored passwords.
- Password policies should not require employees to change passwords on a regular basis
The new guidelines advise against the need for users to change passwords after a specific time period. Instead, passwords should be changed in the event they are exposed, or there is other evidence they’ve been compromised. Requiring periodic password changes was found to lead to predictable behaviors, such as incrementing a root password with numbers or symbols and exposing organizations to brute force attacks and other malicious activities. As they explained in their FAQ, “Users tend to choose weaker memorized secrets when they know that they will have to change them in the near future. When those changes do occur, they often select a secret that is similar to their old memorized secret by applying a set of common transformations, such as increasing a number in the password. This practice provides a false sense of security if any of the previous secrets have been compromised since attackers can apply these same common transformations.”
This represents a major change in prevailing recommendations, aligning with best practices in access management and risk assessment. Even five years since NIST implemented these guidelines, many other frameworks (e.g. PCI, HIPAA, HITRUST) have not yet updated their guidelines to reflect these advancements in digital authentication and identity proofing processes. Organizations that otherwise held to compliance requirements should strongly consider eliminating periodic password expiration for the improvement of user experience, security, and overhead costs associated with password changes.
- Increased character allowance
Although the new guidelines require users to maintain passwords with a minimum of eight characters, they also advocate for password fields to allow up to at least 64 characters. According to the document, increasing password allowance will enable users to utilize passphrases. Passphrases are a sequence of preferably unrelated words. NIST encourages allowing passwords as lengthy as desired, using any characters they like (including spaces), thus aiding memorization. Longer passwords – as long as they do not show up among compromised passwords – provide better security compared to shorter passwords. NIST notes that extremely long passwords (perhaps megabytes in length) could conceivably require excessive processing time to hash, so it is reasonable to have some limit; however, they don’t explicitly list that limit.
- Screen passwords against blacklists to enhance privacy controls
The guidelines also advise screening passwords against lists of commonly used or compromised passwords.
NIST explains, “it is important to discourage the use of very common passwords, particularly those that are most likely to be tried in an online password-guessing attack. Some passwords that meet the requirements of common composition rules are, in fact, quite common (e.g., Password1!), while others that do not meet composition rules are not common at all. The dictionary, or blacklist, should contain likely common passwords without particular regard to how they are composed.”
Through screening, users can avoid selecting exposed passwords that will introduce security risks. Additionally, organizations can monitor existing passwords for exposure since a password that is safe today, can get exposed tomorrow, necessitating continuous risk assessment and mitigation strategies.
Screening for common and compromised passwords – and keeping that up to date – requires a change in mindset and technology approaches to password policies. Previous approaches could rely on simple regular expressions or formulas to determine if a password was safe. The new requirements involve keeping an up-to-date blacklist. The research required for maintaining an accurate list will likely be left to third parties.
Why Every Organization Should Consider Adopting the NIST Password Guidelines
As we reflect on the transformative advances in security since NIST’s updated password guidelines, it’s evident that adopting these recommendations is more than a compliance issue—it’s a step towards smarter, more effective breach prevention. The shift towards user-friendly yet secure password practices is not just about following a set of rules; it’s about embracing a new mindset. For organizations still adhering to outdated methods, the time to act is now. By aligning with NIST’s evolved guidelines, we can enhance both security and user experience, paving the way for a more secure digital future.
Read more:
